Miscreants are actively exploiting two new zero-day vulnerabilities to wrangle routers and video recorders into a hostile botnet used in distributed denial-of-service attacks, researchers from networking firm Akamai said Thursday.
Both of the vulnerabilities, which were previously unknown to their manufacturers and to the security research community at large, allow for the remote execution of malicious code when the affected devices use default administrative credentials, according to an Akamai post. Unknown attackers have been exploiting the zero-days to compromise the devices so they can be infected with Mirai, a potent piece of open source software that makes routers, cameras, and other types of Internet of Things devices part of a botnet that’s capable of waging DDoSes of previously unimaginable sizes.
Akamai researchers said one of the zero-days under attack resides in one or more models of network video recorders. The other zero-day resides in an “outlet-based wireless LAN router built for hotels and residential applications.” The router is sold by a Japan-based manufacturer, which “produces multiple switches and routers.” The router feature being exploited is “a very common one,” and the researchers can’t rule out the possibility it’s being exploited in multiple router models sold by the manufacturer.
Akamai said it has reported the vulnerabilities to both manufacturers, and that one of them has provided assurances security patches will be released next month. Akamai said it wasn’t identifying the specific devices or the manufacturers until fixes are in place to prevent the zero-days from being more widely exploited.
“Although this information is limited, we felt it was our responsibility to alert the community about the ongoing exploitation of these CVEs in the wild. There is a thin line between responsible disclosing information to help defenders, and oversharing information that can enable further abuse by hordes of threat actors.”
The Akamai post provides a host of file hashes and IP and domain addresses being used in the attacks. Owners of network video cameras and routers can use this information to see if devices on their networks have been targeted.
The remote code execution uses a technique known as command injection, which first requires an attacker to authenticate itself using the credentials configured in the vulnerable device. The authentication and injection is carried out using a standard POST request.
In an email, Akamai researcher Larry Cashdollar wrote:
The devices don’t typically allow code execution through the management interface. This is why getting RCE through command injection is needed.
Because the attacker needs to authenticate first they have to know some login credentials that will work. If the devices are using easy guessable logins like admin:password or admin:password1 those could be at risk too if someone expands the list of credentials to try.
He said that both manufacturers have been notified, but only one of them has so far committed to releasing a patch, which is expected next month. The status of a fix from the second manufacturer is currently unknown.
Cashdollar said an incomplete Internet scan showed there are at least 7,000 vulnerable devices. The actual number of affected devices may be higher.
Mirai first came to widespread public attention in 2016, when a botnet—meaning a network of compromised devices under the control of a hostile threat actor—took down the security news site KrebsOnSecurity with what was then a record-setting 620 gigabit-per-second DDoS.
Besides its enormous firepower, Mirai stood out for other reasons. For one, the devices it commandeers were an ensemble of routers, security cameras and other types of IoT devices, something that had been largely unseen prior to that. And for another, the underlying source code quickly became freely available. Soon, Mirai was being used in even larger DDoSes targeting gaming platforms and the ISPs that serviced them. Mirai and other IoT botnets have been a fact of Internet life ever since.
The Mirai strain used in the attacks discovered by Akamai is primarily an older one known as JenX. It has been modified, however, to use many fewer domain names than usual to connect to command-and-control servers. Some malware samples also show ties to a separate Mirai variant known as hailBot.
The code used in the zero-day attacks observed by Akamail—including offensive racist slurs—are almost identical to that used in DDoS attacks a China-based security firm observed targeting a Russian news website in May. The image below shows a side-by-side comparison.
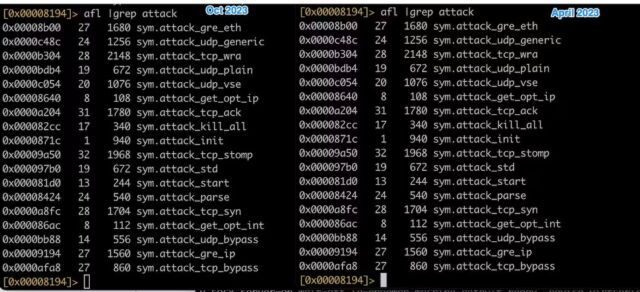
Payloads exploiting the zero-days are:
alert tcp any any -> any any (msg:"InfectedSlurs 0day exploit #1 attempt"; content:"lang="; content:"useNTPServer="; content:"synccheck="; content:"timeserver="; content:"interval="; content:"enableNTPServer="; sid:1000006;)
and
alert tcp any any -> any any (msg:"InfectedSlurs 0day exploit #2 attempt"; content:"page_suc="; content:"system.general.datetime="; content:"ntp.general.hostname="; pcre:"ntp.general.hostname="; content:"ntp.general.dst="; content:"ntp.general.dst.adjust="; content:"system.general.timezone="; content:"system.general.tzname="; content:"ntp.general.enable="; sid:1000005;)
People or organizations concerned with the possibility they’re being targeted with these exploits can use Snort rules and indicators of compromise published by Akamail to detect and repel attacks. At the moment, there is no way to identify the specific devices that are vulnerable or the manufacturers of those devices.